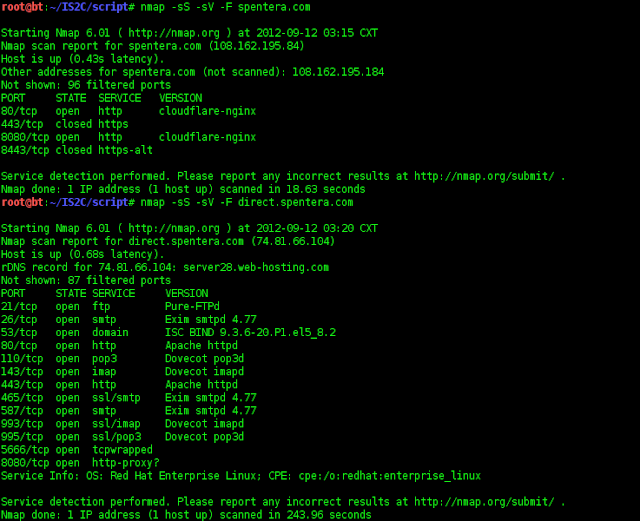
Information Gathering
Today task is to collect information from is2c-dojo.com and spentera.com
Scanning using nmap and found it using cloudflare. Quick seacrh in http://www.cloudflare-watch.org/cfs.html resulting 67.222.154.106.

Result :
[*] Using cloudflare service.
[*] Direct IP 74.81.66.104.
[*] Other subdomain direct, ftp, and project.
Using WPScan for scanning Web App.
Result :
[*] Wordpress version 3.4.2
[#] is2c-dojo.com
Scanning using nmap and found it using cloudflare. Quick seacrh in http://www.cloudflare-watch.org/cfs.html resulting 67.222.154.106.

Result :
[*] Using cloudflare as proxy.
[*] rita.ns.cloudflare.com & ivan.ns.cloudflare.com as the name server with IP 108.162.199.80/180.
[*] is2c-dojo.com has another subdomain. direct, ftp, and mail. with IP 67.222.154.106.
[*] 67.222.154.106 is registered to partnerit.us.
[*] Using privacy protection of WHOIS from http://privacyprotect.org.
Using WPScan for scanning Web App.
Result :
[*] Wordpress version 3.4.1
[*] Directory listing on.
[*] Php error print in web.
[*] username="iscdojon" from full path disclosure.
[#] spentera.com
Result :
[*] Using cloudflare service.
[*] Direct IP 74.81.66.104.
[*] Other subdomain direct, ftp, and project.
Using WPScan for scanning Web App.
Result :
[*] Wordpress version 3.4.2
Cybercrime in Indonesia
Honestly i don't really know much about this very topic.
But i do remember one news long time ago i read in online news site about a guy that is wanted by the police because he pays all the stuff that he bought by using a stolen credit card. The story talks around the police effort and failing to catch this guy. Because the guys just keep moving 'kost to kost'. But now i don't really know about the status of the pursuit.
Another crime i do remember recently about ATM (Automated teller machine) Hacks using a technique called atm skimmer scam. The device is putted in the card slot and designed to be hard to distinguish. The device work is to record anyting from the magnetic plate from the card and later can be duplicate/restore to other card. Clean and simple thus makes people thinks that must be some mastermind behind it. Maybe it just some international syndication or something. i don't know. From two above cases, i may now conclude the more formal aspect, the law. In case 1 of stolen credit card, it was also a identity theft.The second is also identity theft and interception of information.
In Indonesian UUITE :
Pasal 31 (1) Setiap Orang dengan sengaja dan tanpa hak atau melawan
hukum melakukan intersepsi atau penyadapan atas
Informasi Elektronik dan/atau Dokumen Elektronik dalam
suatu Komputer dan/atau Sistem Elektronik tertentu milik
Orang lain.
Pasal 32 (3) Terhadap perbuatan sebagaimana dimaksud pada ayat (1) yang mengakibatkan terbukanya suatu Informasi Elektronik dan/atau Dokumen Elektronik yang bersifat rahasia menjadi dapat diakses oleh publik dengan keutuhan data yang tidak sebagaimana mestinya
Pasal 36 Setiap Orang dengan sengaja dan tanpa hak atau melawan hukum melakukan perbuatan sebagaimana dimaksud dalam Pasal 27 sampai dengan Pasal 34 yang mengakibatkan kerugian bagi Orang lain.
With acumulation of maximum Rp15.300.000.000,00 worth of fined and maximum 30 years of jailtime.
Thanks for reading.
But i do remember one news long time ago i read in online news site about a guy that is wanted by the police because he pays all the stuff that he bought by using a stolen credit card. The story talks around the police effort and failing to catch this guy. Because the guys just keep moving 'kost to kost'. But now i don't really know about the status of the pursuit.
Another crime i do remember recently about ATM (Automated teller machine) Hacks using a technique called atm skimmer scam. The device is putted in the card slot and designed to be hard to distinguish. The device work is to record anyting from the magnetic plate from the card and later can be duplicate/restore to other card. Clean and simple thus makes people thinks that must be some mastermind behind it. Maybe it just some international syndication or something. i don't know. From two above cases, i may now conclude the more formal aspect, the law. In case 1 of stolen credit card, it was also a identity theft.The second is also identity theft and interception of information.
In Indonesian UUITE :
Pasal 31 (1) Setiap Orang dengan sengaja dan tanpa hak atau melawan
hukum melakukan intersepsi atau penyadapan atas
Informasi Elektronik dan/atau Dokumen Elektronik dalam
suatu Komputer dan/atau Sistem Elektronik tertentu milik
Orang lain.
Pasal 32 (3) Terhadap perbuatan sebagaimana dimaksud pada ayat (1) yang mengakibatkan terbukanya suatu Informasi Elektronik dan/atau Dokumen Elektronik yang bersifat rahasia menjadi dapat diakses oleh publik dengan keutuhan data yang tidak sebagaimana mestinya
Pasal 36 Setiap Orang dengan sengaja dan tanpa hak atau melawan hukum melakukan perbuatan sebagaimana dimaksud dalam Pasal 27 sampai dengan Pasal 34 yang mengakibatkan kerugian bagi Orang lain.
With acumulation of maximum Rp15.300.000.000,00 worth of fined and maximum 30 years of jailtime.
Thanks for reading.
VirtualBox Settting Up
Today i'm ganna talk about how to install Oracle's Virtual Box in my backtrack and populate it with the legendary Win XP Operating System, and in the end just try to connect it to host.
1. Installing VirtualBox
There are many ways you can get a copy of the virtualbox package.
- apt-get install virtualbox-4.1
- go to this links https://www.virtualbox.org/wiki/Linux_Downloads and choose ubuntu 10.04
- or just download it in wget http://download.virtualbox.org/virtualbox/4.1.20/virtualbox-4.1_4.1.20-80170~Ubuntu~lucid_i386.deb
Run it from X Menu > System > Oracle VM VirtualBox.
- Click New icon.
- Give it name XP and click next.
- Memory just next.
- Virtual hard disk, creation and details just click next.
- I set the the amount of the new virtual disk about 5 Gig, because i think it already enough.
- Next and create.
Yay!
Now before we start the box, click on the "storage" menu below the display.
3. Installing XP
- Run the box, click "Start ->"
- Ping is successfully done from the virtualbox and using nmap to see if the host is up.
And that is it for today, it's a wrap. Thank you for reading. A long road ahead still waiting to be discovered.
Stay tune you guys.
\m/
1. Installing VirtualBox
There are many ways you can get a copy of the virtualbox package.
- apt-get install virtualbox-4.1
- go to this links https://www.virtualbox.org/wiki/Linux_Downloads and choose ubuntu 10.04
- or just download it in wget http://download.virtualbox.org/virtualbox/4.1.20/virtualbox-4.1_4.1.20-80170~Ubuntu~lucid_i386.deb
and install it using dpkg -i command.
2. Running VirtualBox
Run it from X Menu > System > Oracle VM VirtualBox.
- Click New icon.
- Give it name XP and click next.
- Memory just next.
- Virtual hard disk, creation and details just click next.
- I set the the amount of the new virtual disk about 5 Gig, because i think it already enough.
- Next and create.
Yay!
Now before we start the box, click on the "storage" menu below the display.
and choose our WinXPPro-SP3.iso
- Run the box, click "Start ->"
 |
| Windows Installer Started |
 |
| Formatting the virtual hard drive |
 |
| Installing new look |
Now the installer ask for Product Key, eventhough the key is in the iso, i'm just too lazy to mount it, so yeah grandpa Google is our friend.
 |
| Just use pro retail |

Windows XP warm welcome
And the first thing i do is to activate the system using "antiwpa3".
.
4. Connecting
- Check the ip using ipconfig and the ip address is : 10.0.2.15
- Try to ping it using ping command to the ip address from the host.
 |
| Still No luck |
- And then i try to change "Network Adapter" setting to "Bridged Adapter" and run ipconfig again.
 |
| Notice the IP diffrence. |
 |
| Host is up |
- Ping is successfully done from the virtualbox and using nmap to see if the host is up.
And that is it for today, it's a wrap. Thank you for reading. A long road ahead still waiting to be discovered.
Stay tune you guys.
\m/
resolve ip
Untuk mengetahui alamat ip sebuah url bisa dengan ping, bisa juga dengan ini.
tapi yang keren disini, kita pake ip addres yg diatas untuk mengetahui server apa yg terkait dengan ip tersebut.
host -t A akakom.ac.id
akakom.ac.id has address 110.76.151.2
2.151.76.110.in-addr.arpa domain name pointer ns.akakom.ac.id.
2.151.76.110.in-addr.arpa domain name pointer mail.akakom.ac.id.
Syntax Highlighter
Mencoba mengimplementasikan Syntax Highlighter di blogger ini,
Dengan memasukan kode ke template blogger :
dan memasukan code di posting dengan tag berikut
Smoga bisa.
Dengan memasukan kode ke template blogger :
<!--SYNTAX HIGHLIGHTER BEGINS-->
<link href='http://alexgorbatchev.com/pub/sh/current/styles/shCore.css' rel='stylesheet' type='text/css'/>
<link href='http://alexgorbatchev.com/pub/sh/current/styles/shThemeDefault.css' rel='stylesheet' type='text/css'/>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shCore.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushCpp.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushCSharp.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushCss.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushJava.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushJScript.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushPhp.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushPython.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushRuby.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushSql.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushVb.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushXml.js' type='text/javascript'></script>
<script src='http://alexgorbatchev.com/pub/sh/current/scripts/shBrushPerl.js' type='text/javascript'></script>
<script language='javascript'>
SyntaxHighlighter.config.bloggerMode = true;
SyntaxHighlighter.config.clipboardSwf = 'http://alexgorbatchev.com/pub/sh/current/scripts/clipboard.swf';
SyntaxHighlighter.all();
</script>
<!--SYNTAX HIGHLIGHTER ENDS-->
dan memasukan code di posting dengan tag berikut
Dan character html harus di escape dulu biar gak error. Di sini Quick Escape
<pre class="brush:html">
HTMLmu disini
</pre>
Smoga bisa.
Langganan:
Postingan
(
Atom
)